Living, Learning and Connecting in Cyberspace
We increasingly rely upon networked technologies and the internet infrastructures upon which these rely; the myriad miles of fibreoptic cables, the banks of servers, the lofty data centres and the ever-encircling satellites. However, these integral systems are often unseen, overlooked, and sometimes intentionally concealed. Additionally, the software and hardware that we see in our everyday environments – laptops, desktops, smartphones, smart devices and so forth – are often so entrenched in our way of being that we overlook our reliance upon them until they stop functioning; a power cut, server downtime, an empty battery.
This competition focused on photograph submissions that engaged with the human experiencing of cyberspace and its interconnected hardware and software. Submitted photos aimed to capture a moment that told a story about living, learning and connecting in cyberspace.
Submitted photographs were eligible for two awards in three categories: Kent students, Kent staff, and non-Kent UK residents. The awards are ‘Best Overall Image’ and ‘Most Creative Image’. We are delighted to showcase the winning photos.
Kent Student Winners
Best Overall
Security or privacy – you need both, by Md Rezwan Hasan, PhD Student in Electronic Engineering in the School of Engineering
“This photograph depicts a scenario where users are connecting to cyberspace while ensuring security and privacy. To achieve privacy, they are using a webcam cover and anti-virus for security. The theme illustrates that we need both physical devices and software-based applications to protect ourselves while engaging in cyberspace.”
Most Creative
Apple biometric facial unlock, by Joe Edmunds, MSc in Cyber Security with an Industrial Placement and is with the School of Computing
“Face ID is a new technology that millions of people use to unlock their most personal device. This biometric authentication uses Infra-Red and Dot Projection to accurately map out the unique features of our faces and textures of our skin, to securely authorise us. This process is viewable from a cameras’ perspective, but invisible to the naked eye.”
Kent Staff Winners
Best Overall
Keeping data safe, by Mickey Williams.
“Keeping data safe is a core aspect of working in a digital space. The University takes great care to make sure all of the data we store is recoverable in any unforeseen situation. Every week the University backs up just over 300 terabytes (300,000 gigabytes) of data to magnetic tapes, which are then stored securely off-campus. Each individual tape can store 5.5 terabytes of data but only 30 tapes can be exported at a time. In this photo you can see 30 tapes totalling 165 terabytes being unloaded from the tape library ready to be moved off-site.”
Most Creative
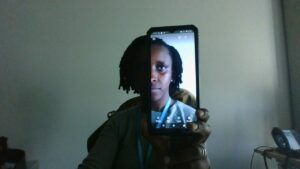
Online persona, by Akaliza Keza Ntwari.
“The image represents our online persona. It shows two sides of the face – one a bright photo, and the other, in shadow. [How] we present online persona can often be different to how we are offline, and some people we interact with online will never get to see this other side of us. I created the image with my mobile phone and my laptop.”
Non-Kent UK Residents
Best Overall
Beneath the screen, by Anna Dyson.
“This image explores our deep-rooted and often unconscious dependence on connected devices. It seeks to capture the intertwined nature of humans and their smartphones, which sometimes feel like an essential part of, or even extension of ourselves. Smartphones can be a portal to the wider world, giving us access to goods, services, and social spaces at our fingertips. But they can also be a portal into us as people. This image therefore also tries to capture the way in which the human experience of cyberspace through the smart phone translates to a series of valuable data points. With such dependence on our smart devices, it can be easy to overlook the data we sometimes unknowingly offer up about our lives and the ways this data might be harvested or exploited. Similarly, it can be easy to overlook the complex array of components, networks, and activity that goes on beneath the surface of that glossy screen, even when it is not in use.
I’ve created this image by combining human and computational processes: running a software algorithm on my original photograph using visual processing software. The algorithm builds up layers of the original photographic data in thin strands. I then mapped this back onto the initial photograph using multiple layers. The idea behind this approach was to try and visually emulate the intricate web of networked activity and data underpinning the intertwined human-smartphone relationship.”
Most Creative
Kayla goes online – the internet of dolls, by Lynsay Shepherd.
“Kayla, the IoT doll goes online. This photo was taken in a hotel room whilst travelling across Scotland for a series of fun, educational cybersecurity Christmas lectures for school children. These lectures promoted cybersecurity as a potential career path.”
Runners up
Best Overall
Data security, by Les Minchinton-Smith.
Connecting the campus together, by Marc Greenhill-Jeffery.
Back to the future, by Anthony Phipps (member of iCSS External Advisory Board).
An unattended office PC, by Nandita Pattnaik (iCSS PhD Student).
Most Creative
3019, by Georgia Janes.
Higher power, by Huaiyuan Ren (PhD student, School of Arts, University of Kent).
The shade, by Al Amin Usman Muhammad.
Working from home, by Karen Martin.